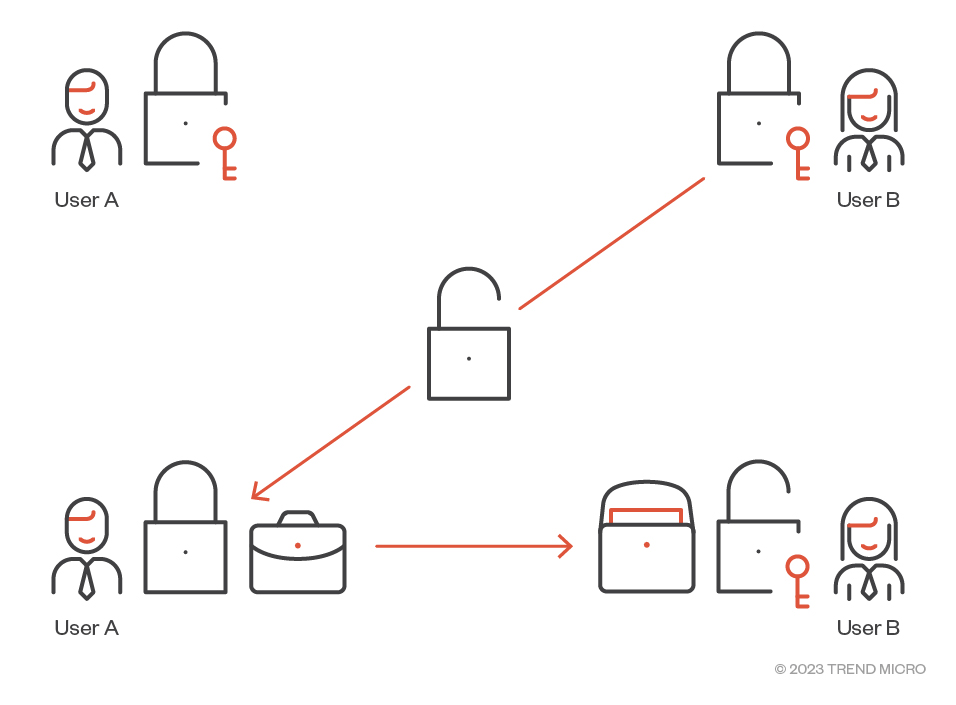
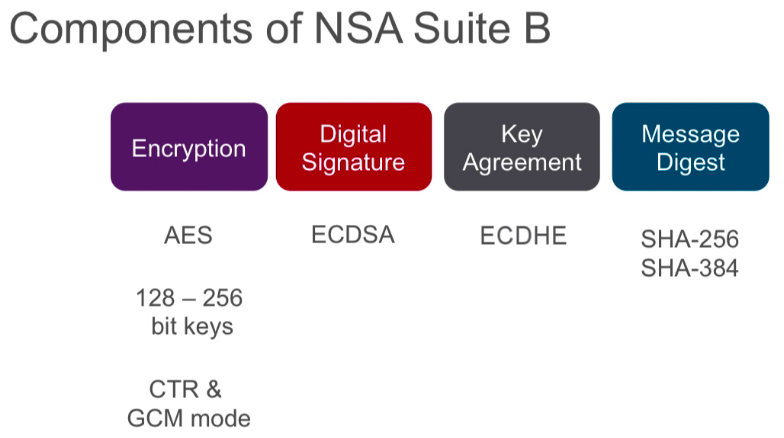
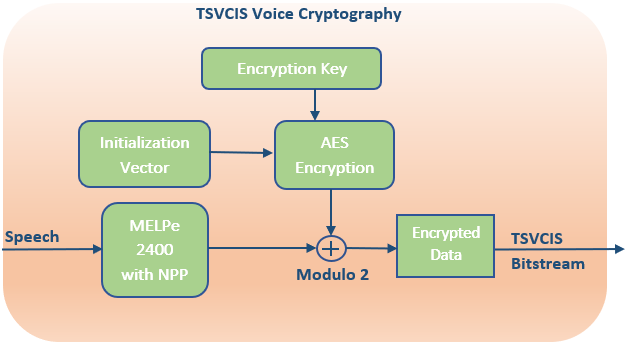
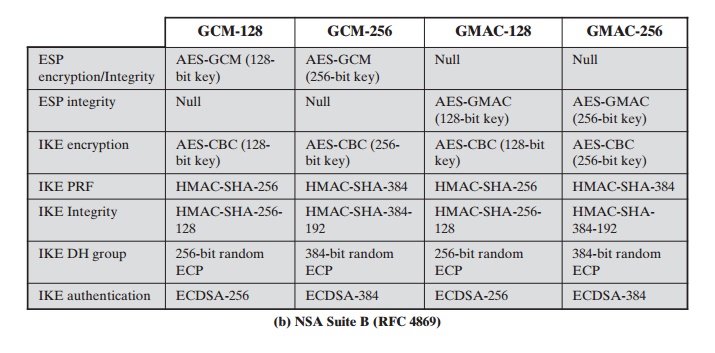
More than just cryptography: The performance advantages of Suite B compliance - Military Embedded Systems
More than just cryptography: The performance advantages of Suite B compliance - Military Embedded Systems

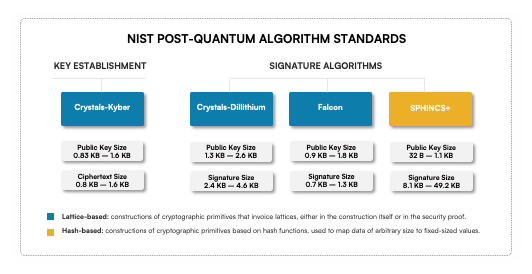
NSA Releases Future Quantum-Resistant (QR) Algorithm Requirements for National Security Systems > National Security Agency/Central Security Service > Article

A. Steffen, CryptoStrength.pptx 1 Information Security 2 (InfSi2) Prof. Dr. Andreas Steffen Institute for Internet Technologies and Applications. - ppt download
GitHub - westerndigitalcorporation/sweet-b: Sweet B is a safe, compact, embeddable library for elliptic curve cryptography.

NSA Suite B Crypto, Keys, and Side Channel Attacks: Pankaj Rohatgi Mark Marson | PDF | Cryptography | Crime Prevention
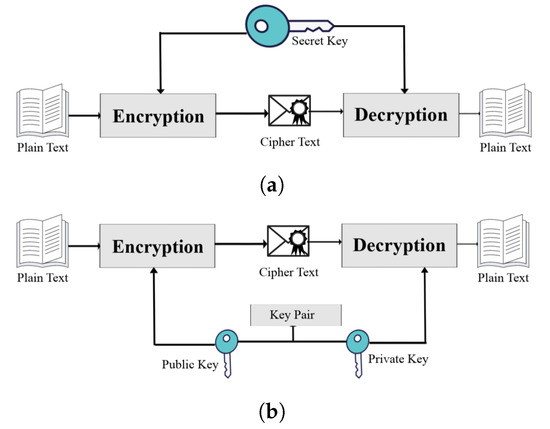
Sensors | Free Full-Text | Resilience Optimization of Post-Quantum Cryptography Key Encapsulation Algorithms